How does ingress filtering stand up to DoS attacks?
By Hiba Eltigani, MANRS fellow
Denial of Service (DoS) attacks have been a common feature of the Internet since its early days. What makes this kind of attack so persistently disruptive, and what can we do to stop them? While not watertight, ingress filtering can provide a sustainable solution – if we’re all willing to work together to apply it across the board.
A short history of DoS attacks
The Internet was commercialized in the early 1990s, but it wasn’t until almost a decade later that the public became aware of DoS attacks. There’s some confusion around the date of the first DoS attack. Some say it was in 1996 when Panix, a US-based ISP, was attacked, others believe it was the Mafia Boy attack on famous websites like CNN, Yahoo and eBay back in 2000. Others claim that it was as long ago as 1974.
While we might not agree on when the first DoS attack happened, we can agree that DoS attacks are one of the most common cyber security threats. They’ve stood the test of time and shown no signs of tapering off. Over time, attackers have become very skilled in exploiting vulnerabilities in protocols, applications, and machines. From Address Resolution Protocol (ARP) poison and synchronize (SYN) flood to Apache2 and Internet of Things (IoT) devices, the aim is to overwhelm the target and take it down.
As machines become more resilient, links have multiplied in number, and DoS attacks have increased in complexity and size. An attack in June, 2020 on an unidentified AWS customer holds the trophy for the largest recorded attack in terms of traffic, with 2.3 Tbps (~55M packet per second (PPS)) at peak. However, an attack reported by Akamai in the same month is not far behind with 418 Gbps (809M PPS), the largest recorded attack in terms of PPS.
The dark heart of DoS attacks
IP source spoofing is at the heart of DoS attacks, especially the distributed denial-of-service attack, famously known as DDoS. Attackers use spoofing to mask their identities and make it difficult to trace them, or to amplify the assault through reflection for maximum damage. Network elements such as open domain name server (DNS) resolvers, network time protocol (NTP) servers, Memcached servers and connectionless lightweight directory access protocol (CLDAP) servers are examples of network nodes used for reflection.
The attacker will send a series of spoofed packets using the targeted network IP address as a source IP, and the network element will reply to what seems a legitimate request. The targeted network will start receiving responses for requests it has not sent, which will eventually consume the available resources and degrade the service for legitimate users.
Defence against DoS attacks
Companies use multiple tactics to ensure increased resilience against DDoS, for example:
- having a bigger bandwidth than they use
- blocking selected ports, protocols, and IP address prefixes for specific network elements
- trying to distribute as much of their services as possible
- contracting cyber security firms for defence
Despite increased success in mitigating the attacks, there is no end in sight. In addition to defending our networks against attacks, we should ensure they’re not used to attack others. Implementing ingress filtering is our best shot.
How does ingress filtering work?
Ingress filtering enables a network to allow only traffic from trusted sources to traverse their networks. So, traffic from a customer with prefix “x” will be allowed, while any other unrecognizable prefixes will not. This practice was coined as a standard by IETF in 1998 following a resurgence of DoS attacks. It was listed in Internet Best Current Practices “BCP 38” in 2000.
“Ingress filtering significantly reduces the probability of using an operator’s network to launch an attack.”
Ingress filtering significantly reduces the probability of using an operator’s network to launch an attack. However, it is redundant if the attacker chooses to use their own legitimate prefix. But is it as simple as that? In fact, no, it’s not.
Access lists, which can be used for implementation, require manual entry of the permitted prefix for each customer and must be applied to each corresponding interface. This process is tedious, unscalable and hard to maintain, which contradicts the principles of good operation management. An alternative is the use of reverse-path forwarding (RPF) for dynamic filtering. This simplifies the operation, but can block legitimate traffic if not implemented correctly. Adopting policies like asymmetric routing, where a provider sends traffic through one link but receives it through another one, poses issues and leaves operators struggling with how to implement reverse-path forwarding without compromising their customers’ traffic.
Since 2004, the IETF has published several updates on how to implement filtering using RPF and accommodate as many routing scenarios as possible. In essence, routers’ data about routes and forwarding interfaces can be used to inform filtering decisions and cater for different scenarios. Vendors have provided variant implementations, but the work is far from done. The latest update is RFC 8704, published in February 2020. It introduced enhanced feasible-path unicast reverse path forwarding’, in an effort to strike a better balance between flexibility and efficiency. Today, the two best practices, BCP 38 and BCP 84, are available for ingress filtering implementation.
What’s the future for ingress filtering?
Ingress filtering has a long way to go, as shown in the graphs below. The majority of network operators may be implementing the recommendation, but those who are not yet doing so undermine the security of the whole Internet. This is particularly true due to the rise in cyber security threats, spread of unsecured IoT devices and the monetization of cyber security attacks.
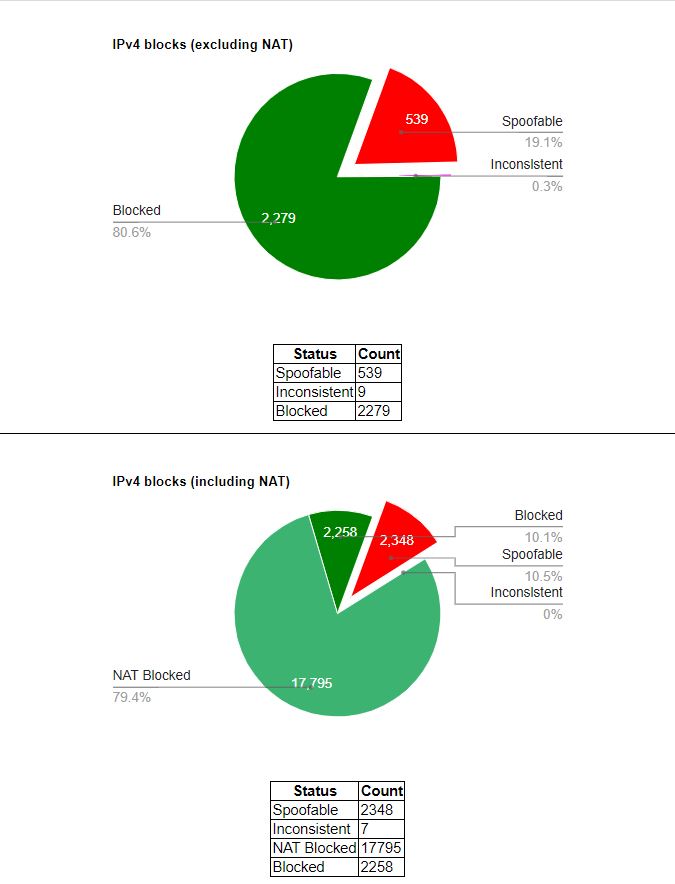
“We should all deploy ingress filtering to combat cyber security threats and enhance networks’ resilience.”
It comes down to how each individual network upholds its responsibility and does its part for the common good. We should all deploy ingress filtering to combat cyber security threats and enhance networks resilience. It’s also good practice to protect the reputation of your IP prefixes and look after your customers’ interests.
For these reasons and more, standards like BCP 38 and BCP 84 implementation are at the heart of the MANRS initiative, where all participants pledge their commitment for routing security. If we’ve learned anything from these difficult times, it’s that we need to work together to succeed.
Learn more about the MANRS Network Operators programme and join us in protecting the core of the Internet!
Editor’s Note: This is a guest post by one of the MANRS Fellows. Fellows are emerging leaders who strongly believe that routing security is an essential component for the future well-being of the Internet and are ready to contribute to its improvement.
Leave a Comment