Explainer: US Government Activity and BGP Security

This post is part of our MANRS Basics series. It is intended for non-experts who are interested in learning more about routing security terms and events with reasonably simple explanations.
Several high-profile Internet routing incidents have caused some governments to investigate how they can clean up their networks and the global routing system, including in the United States. As covered in this MANRS blog post in April 2023, overall deployment of RPKI in the US has started to catch up with the global average, but US Government networks are still lagging behind, as shown in Figure 1:
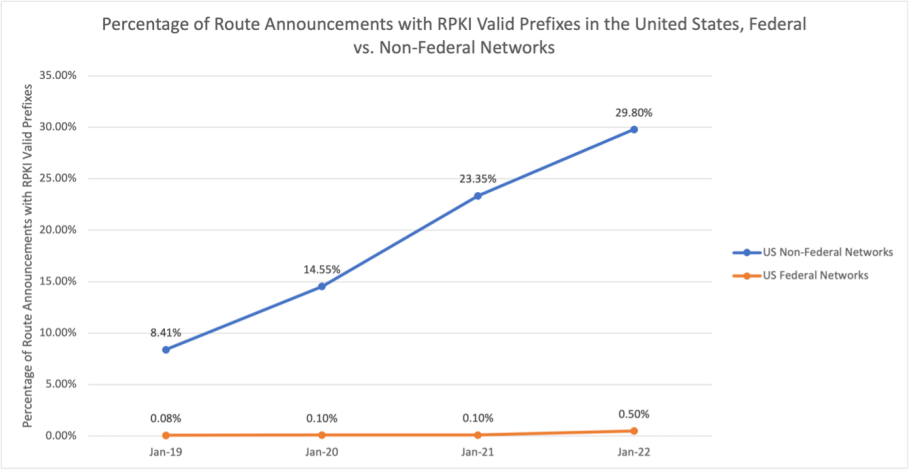
This is why it’s such good news that the US Department of Commerce’s National Telecommunications and Information Administration (NTIA) alongside several other bureaus within Commerce including the Bureau of Economic Analysis (BEA), the Bureau of Industry and Security (BIS), the National Oceanic and Atmospheric Administration (NOAA) and the International Trade Administration (ITA), began implementing RPKI. This should cause a huge spike in the orange line above in Figure 1 to bring more US Federal networks in line with the private sector.
Where does regulation fit into all of this?
While the US Department of Commerce is making great strides in routing security, the US Federal Communications Commission (FCC) is suggesting that regulation might be more of an incentive to clean up routing security.
A quick timeline of the US government’s most recent involvement with BGP security:
- 11 March 2022 – the Federal Communications Commission (FCC) released a Notice of Intent (NOI) on routing security. A notice of inquiry is a proceeding where the U.S. government is merely asking questions.
- 12 April 2022 – the Internet Society (ISOC), then-Secretariat of MANRS, responded to the NOI. Read the full filing or the blog post summary.
- 2 March 2023 – the US National Cybersecurity Strategy identified routing security as a “pervasive concern” and called on the US federal government to implement routing security. (MANRS Observatory data observes US federal networks significantly lagging behind their.)
- 31 July 2023 – the FCC and CISA held a BGP Security Workshop noting that we must work together to develop and implement industry standards and best practices to reduce route hijacks and leaks. MANRS participants actively contribute to this workshop.
- 1 January 2024 – the Global Cyber Alliance took over the MANRS secretariat role, with continued policy and advocacy support from ISOC.
- 4 April 2024 – In a “Declaratory Ruling” the FCC implied its intention to regulate BGP.
- 17 April 2024 – GCA and ISOC filed a joint response, and MANRS, GCA, and ISOC each highlight why regulating BGP is not helpful.
- 13 May 2024 – the US Department of Commerce held a “Route Signing Day” highlighting the renewed effort to implement RPKI in response to the National Cybersecurity Strategy. ISOC summarizes this major milestone well.
- 15 May 2024 – the FCC filed a Notice of Proposed Rulemaking (NPRM) on Routing Security Reporting Requirements.
- Ongoing – The National Institute of Standards and Technology (NIST) continues to collaborate with the Internet engineering community to advance new routing security standards, and continues to operate the NIST RPKI Monitor.
We recently outlined five reasons regulating BGP is a bad idea.
What is the alternative?
Instead of regulation, we fully believe in the ability of the global technical community of routing security experts to work in a coordinated and collaborative way to continue improving routing security practices. Just this month, we reached a major milestone: For the first time in the history of RPKI, the majority of IPv4 routes in the global routing table are covered by ROAs, according to the NIST RPKI Monitor. The drive for collective action by the telecommunications industry, without regulation, is already moving the needle significantly.
We are thrilled to see the US Department of Commerce taking key steps to prioritize routing security, and encourage everyone else who runs a network to do the same. If you operate a network, you should look at the Actions called for in the MANRS Programs for Network Operators, Internet Exchange Points (IXPs), CDN and Cloud Providers, and Equipment Vendors, and join the community of security-minded organizations that make the Internet better for us all.
Leave a Comment