MANRS+ Concept
The Internet is made up of more than 75,000 independent networks, including those run by enterprises, universities and schools, government agencies, broadband and mobile access providers, and connectivity providers offering transit services to their customers.
Each network exchanges routing information – how packets of data move across the Internet – that contributes to building a roadmap of the Internet. If left unsecured, this information can be tampered with or incorrectly updated, resulting in traffic being dropped, inspected, or diverted or leading to DDoS attacks or strained infrastructure, all of which can cost a business time, money, and reputation.
Securing routing information is a shared responsibility. Each network must implement basic routing security techniques on its own network and monitor its network neighbors to allow only legitimate traffic. Unfortunately, the level of awareness and business case for implementing routing security measures is often not strong enough.
An industry-led initiative called Mutually Agreed Norms for Routing Security (MANRS) establishes a common baseline of specific actions for each network type. It builds a community of security-minded network operators that meet MANRS conformance and transparency requirements. More than 1,000 networks are already MANRS participants.
MANRS+
A second, elevated tier of MANRS participation is being developed to increase awareness and participation among enterprises, requiring connectivity providers to comply with more stringent provisions and auditing. It creates a more robust business case for routing security for connectivity providers while engaging their potential enterprise customers by raising awareness, generating demand, and providing necessary tools for security assurance.
The MANRS+ main principles are:
- More substantial and more detailed requirements in traffic security, mitigating a broader set of risks.
- Higher levels of auditing to ensure conformance.
- More focus on what enterprise customers need.
It is important to note that MANRS remains an essential component of MANRS+. The real value of MANRS is that it creates a norm — a common baseline that can be diffused through the ecosystem and used to raise awareness.
MANRS+ can be helpful in a variety of scenarios. Each use case below focuses on a specific set of requirements.
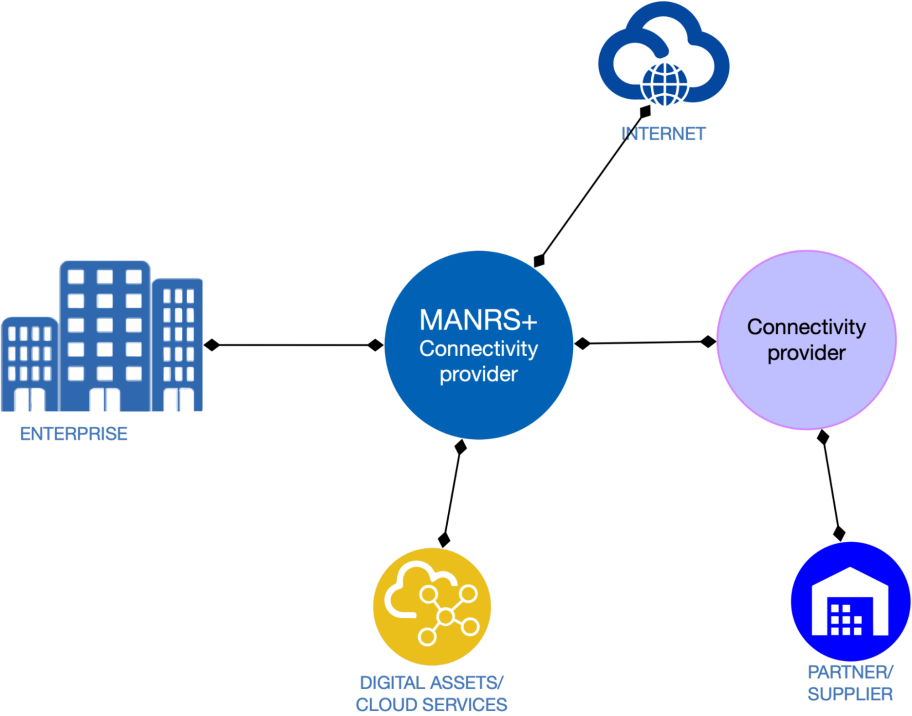
An enterprise (for example, a business or university), a cloud provider, or an access ISP recognizes inherent threats from being connected to the Internet. It ensures that their connectivity providers have sufficient controls and services to mitigate these risks.
When a network operator (an enterprise network or an access ISP) is looking for a new IP transit provider, their request for proposal includes a requirement for being ‘MANRS+ certified’ that would make sure the bidding provider has implemented best practice routing security capabilities.
This use case includes the following requirements:
- Routing security – A connectivity provider maintains the capability to detect and mitigate the risk that the relying party’s traffic will be hijacked or detoured on networks they control because of a mistake or an attack.
- DDoS attack protection – A connectivity provider maintains detection and mitigation capabilities to reduce the risk of a volumetric DDoS attack.
- Security Services – A connectivity provider offers security services to help the enterprise maintain a strong security posture and increase the efficacy of the connectivity provider’s security controls. Such services may include performing router security settings (for example, based on CIS benchmarks) and routing incident monitoring and reporting.
Both cloud providers and their customers need a secure value chain between them to make sure their data is safe. A MANRS+ connectivity or cloud provider implements best practice routing security capabilities valuable for both the cloud provider and the end customer (enterprise). The end customer (enterprise) looks for a MANRS+ connectivity provider, and cloud providers recommend MANRS+ connectivity providers to their customers.
This use case includes the following requirements:
- Routing security – A connectivity or cloud provider maintains the capability to detect and mitigate the risk that the relying party’s traffic will be hijacked or detoured on networks they control because of a mistake or an attack.
- Anti-spoofing protection – A connectivity or cloud provider prevents traffic from their direct customers or peers with spoofed source IP addresses.
- Security Services – A connectivity provider offers security services to help the enterprise maintain a strong security posture and increase the efficacy of the connectivity provider’s security controls. Such services may include performing router security settings (for example, based on CIS benchmarks) and routing incident monitoring and reporting.
Networks want to mitigate risks from peering interconnections with other networks. To do so, networks will prefer MANRS+ connectivity providers in their peering arrangements.
This use case includes the following requirements:
- Routing security – A connectivity provider maintains the capability to detect and mitigate the risk that the relying party’s traffic will be hijacked or detoured on networks they control because of a mistake or an attack.
- Routing information – A connectivity provider has accessible, complete, and up-to-date documentation of its routing policy necessary for implementing adequate controls by other network operators.
- Anti-spoofing protection – A connectivity provider prevents traffic from their direct customers or peers with spoofed source IP addresses.
Contact us if you need assistance assessing your routing security risk or to discuss becoming a MANRS participant.