A Regional Look into BGP Incidents in 2020
By Augusto Mathurin, MANRS Fellow (2020 Cohort)
While the MANRS team has already covered Border Gateway Protocol (BGP) security and the MANRS Year in Review for 2020, we can analyze BGP incidents gathered from different sources and through different lenses. In this post, I dig deeper into the incidents by considering them by region and in perspective.
Let’s start with the big ones. The following are five of the most important routing incidents from last year:
- On April 1, 2020, AS12389 (Rostelecom) hijacked multiple prefixes from the largest cloud networks. For about an hour, the ISP announced prefixes belonging to Akamai, Amazon AWS, Cloudflare, Digital Ocean, and Hetzner, among other famous names.
- On July 21, 2020, Brazilian AS264462 (“Comercial Conecte Sem Fio Ltda me”) leaked massive 13046 network prefixes in a networking incident that lasted for more than one hour. AS264462 had no dependent networks, but during the leak, 72 Autonomous Systems were rerouted through it.
- On July 30, 2020, AS10990 (ATLDC – Tulix Systems, Inc.) started announcing invalid prefixes several times. These erroneous announcements lasted for almost an hour and in total six countries and 285 prefixes were affected. This hijack was likely caused by BGP optimizer software.
- On August 24, 2020, AS42910 (Premier DC) leaked 1403 prefixes, mainly from the United States (including Akamai prefixes) and then almost all from Western Asia. The incident lasted for more than four hours, repeating several times.
- On September 29, 2020, AS1221 (Telstra) announced almost 500 prefixes in a BGP hijack event that affected 266 other ASNs in 50 countries, with the most damage rendered to the United States and United Kingdom based networks. The incident lasted for almost three hours, and some high-profile names like ProtonMail were affected.
Most BGP incidents are short-lived and have limited impact on the Internet. However, whether from accidental misconfiguration or malicious attacks, the results are often more than just inconvenient. Now that the MANRS Observatory has more than two years of routing incidents data, let’s take a look!
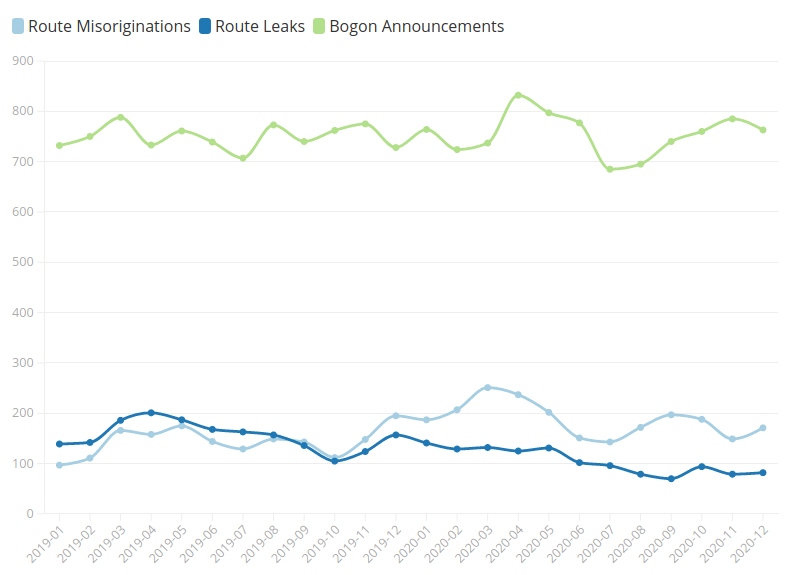
Source: MANRS Observatory
In Figure 1, we see that there is not a dramatic difference between 2019 and 2020, though there is a slight increase in the number of route misoriginations, or hijacks, and a slight decrease in leaks. Figure 2 below shows there were 1,727 hijacks and 1,865 leaks registered in 2019. In 2020, there were 2,255 hijacks (30.57% more) and 1,260 leaks (32.44% less).
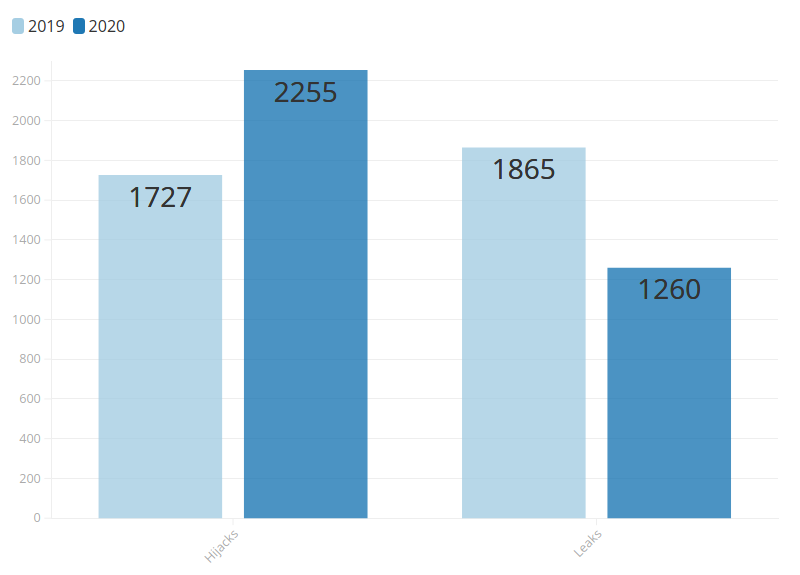
Source: MANRS Observatory
In Figure 3, analyzing the data by Regional Internet Registries (RIRs), we see the same trend: in 2020, there were more hijacks and fewer leaks across all RIRs, with the exception of AFRINIC, which saw the number of leaks climb in 2020.
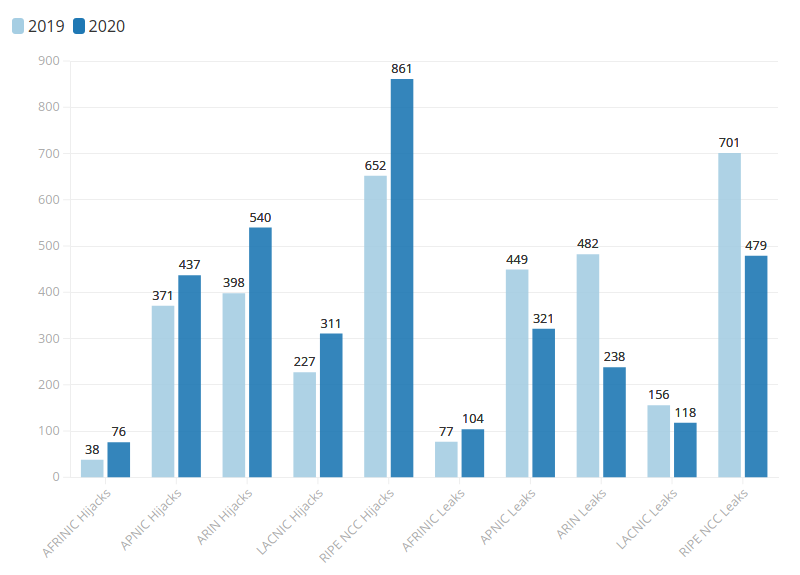
Source: MANRS Observatory
Simply comparing the number of incidents per year by RIR might paint a misleading picture, because new Autonomous System Numbers (ASNs) are registered every day, and some RIRs handle more resources than others. So, if we put things in perspective, even a flat trendline over time is in fact a positive development. In Figure 4, we consider the incidents per 1,000 registered ASNs by region in 2019 vs 2020.
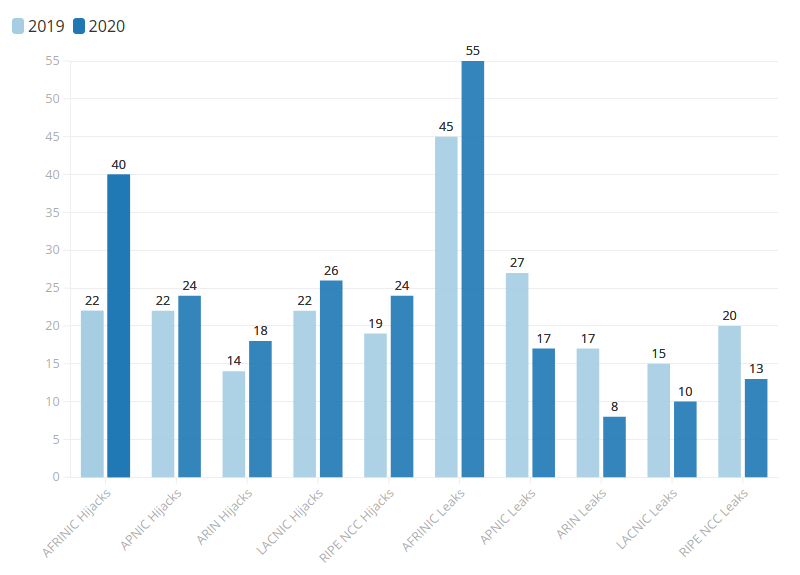
Sources: MANRS Observatory, Telecom SudParis
While the increase in the number of BGP hijacks remains, the improvement on leaks is considerable. If we compare the data across RIRs, we can see that all of them improved on leaks, except AFRINIC. It is true that this RIR has the lowest absolute numbers of leaks and hijacks in both years, but it must be said that they are clearly behind other regions in relative terms, as we can see in Figure 4.
APNIC, ARIN, LACNIC, and RIPE NCC all decreased their number of leaks, both absolutely and relatively, but they had more route misoriginations in 2020 than in 2019. There is obviously still room for improvement, so the commitment to routing security should continue and get even stronger in the future.
Lastly, let’s remember that not everything was captured by numbers and charts. 2020 was a year full of development, milestones achieved, and new participants in MANRS.
Since the beginning of 2020, Google started to contact proactively its peers to alert them about routing information that appears invalid. In May, Team Cymru was the first cybersecurity partner to join MANRS. In December, China Telecom and DigitalOcean also joined.
In 2020, MANRS launched the CDN and Cloud Programme, along with several prominent technology companies, including Verisign, Google, Microsoft, and AWS. In partnership with Global Cyber Alliance, MANRS announced a global study to understand the current state of routing security concerns as well as tool and practice – please take the survey!
In April, MANRS announced it has more than 300 ISPs, and in December, it hit the 500 members milestone.
Keeping the Internet highways clean and secure is hard work, and it takes a strong commitment from all network operators around the world. We should build on all this hard work, and support more networks to join MANRS to protect the core of the Internet together.
Editor’s note: This is a guest post by a MANRS fellow. Viewpoints expressed in this post are those of the author’s and may or may not reflect official positions.
Leave a Comment