Did Ukraine suffer a BGP hijack and how can networks protect themselves?
On 15 February 2022, several high-level Ukrainian services including the Ministry of Defence and two large national banks were targeted with DDoS (Distributed Denial of Service) attacks. Financial services were disrupted for several hours. The attacks did not critically affect the targets, but these incidents alarmed Ukrainian authorities and citizens and served as an international wake-up call to the importance of the Internet’s routing system and the need to protect it.
Across the region, DDoS attacks and BGP hijacks continue to sporadically disrupt services (you can learn more about Border Gateway Protocol (BGP) and BGP hijacks here). Many are talking about how to remove Russia from the Internet, or how to protect the infrastructure in this region from further attacks.
But what happened here? We’ve seen prominent members of the international community, including Bart Groothuis, a Member of the European Parliament, mention that there were incidents of BGP hijacks involving the two countries. It is important to look into the details and examine what really happened.
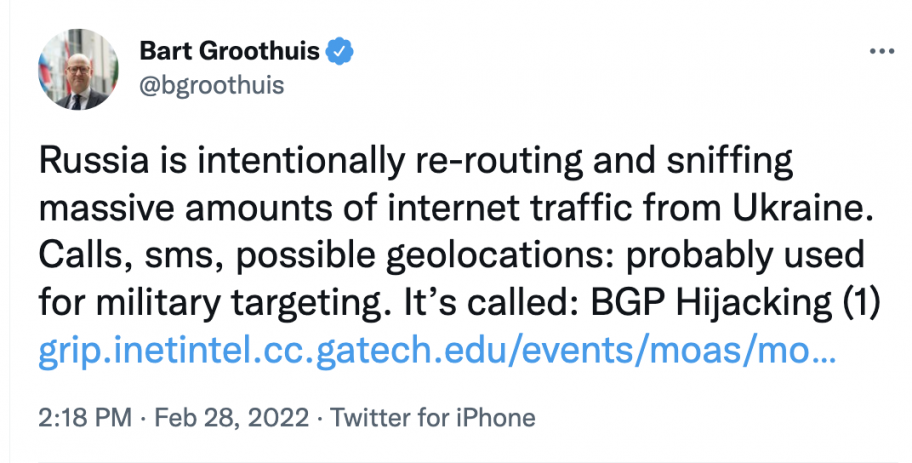
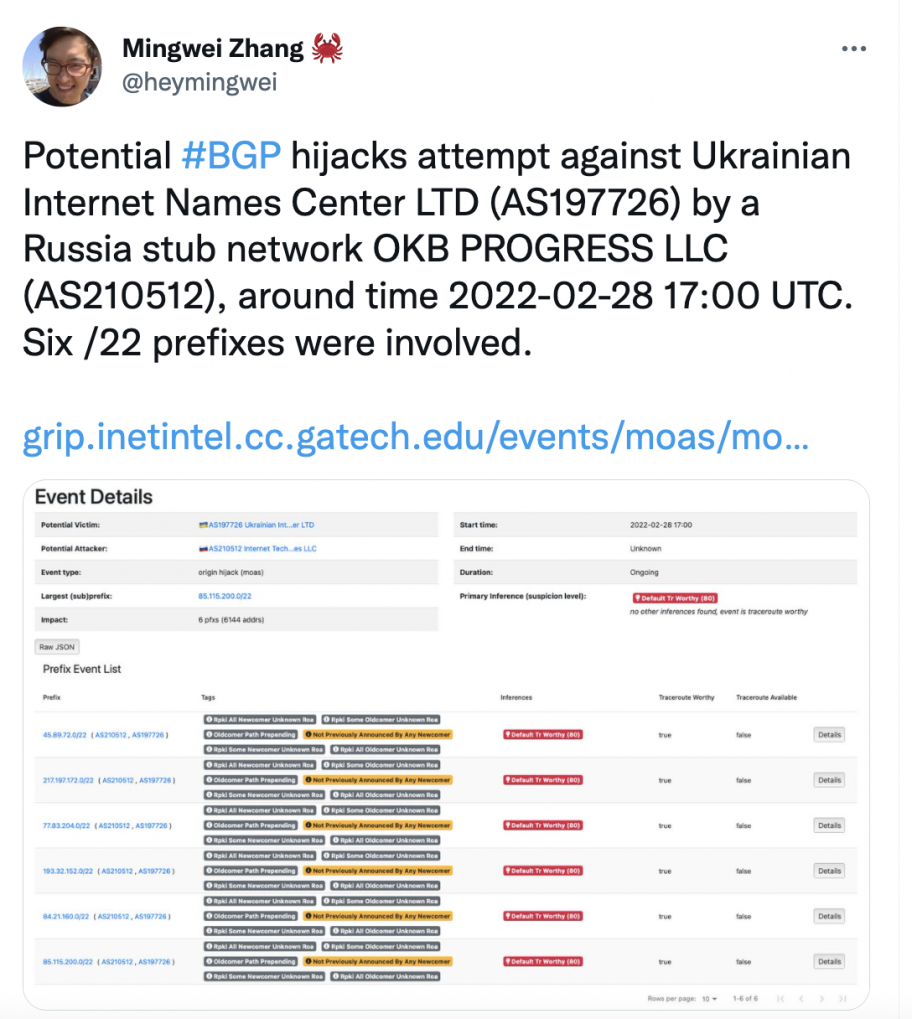
On 28 February, five routes which were originally in use by an entity in Ukraine (AS197726) were announced by another entity in Russia (AS210512). These looked like BGP hijacks and triggered some alerts designed to detect such hijack events.
But upon further review, these were not actually hijacks, but transfers of IP resources after what seemed to be the end of a lease term. Here is one of the first mentions of this explanation:
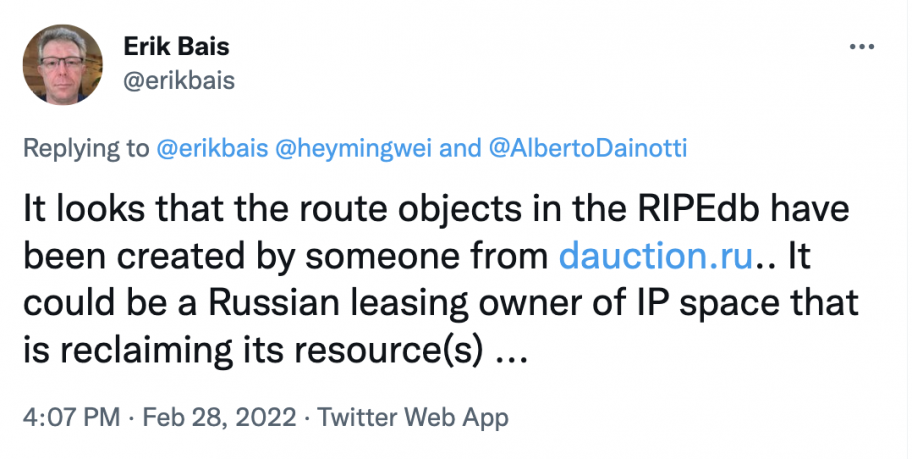
Internet Routing Registries (IRRs) like the RIPE Database use “route objects” to validate the BGP data that networks see. Here is the route object for 45.89.72.0/22, the stub network mentioned in the tweet above:
% Information related to ‘45.89.72.0/22AS210512’ route: 45.89.72.0/22 origin: AS210512 mnt-by: IP-RIPE created: 2022-02-28T12:42:55Z last-modified: 2022-02-28T12:44:32Z source: RIPE
Creating route objects requires the network to pass some level of authentication in the RIPE database. Therefore, this route object tells us that AS210512 is allowed to originate – or announce – via BGP the network 45.89.72.0/22. This route object helps us understand that AS210512 is the rightful holder of this resource. Absent this route object, it would be difficult to understand what happened unless you asked the entities directly.
This shows how important it is to have publicly verifiable information. This is what MANRS Action 4—Global Validation—is all about. More than 750 MANRS participants have made the commitment to keep their routing information up to date.
While it is natural for the world to be on full alert for any incidents that may impact the Internet now, it is important to make sure we avoid causing confusion, which may negatively impact the overall security and stability of the Internet, directly or otherwise.
How Do We Prevent BGP Hijacks?
BGP hijacks have become a common threat, taking advantage of the vulnerability that BGP is inherently based on trust between network operators and cannot verify which network is legitimately permitted to announce which routes.
There are multiple mechanisms available to help BGP make the right decision, but they all rely on the information a network operator provides about its network either through IRR (Internet Routing Registry) or via RPKI (Resource Public Key Infrastructure).
Every network operator should make its routing information globally accessible to facilitate verification and validation. Creating “IRR-Route Objects” and “RPKI Route Origin Authorizations (RPKI-ROAs)” are the two ways to provide publicly verifiable information that you are legitimately announcing these routes and anyone else using your routes are, in fact, hijacking it and should be stopped.
If you are a network operator and want to protect your route advertisements from hijacking, then you must create accurate IRR-route objects and RPKI-ROAs for all of the routes you are advertising from your network. Many networks across the globe don’t allow any routes that don’t have correct routing information in the form of IRR-route objects, RPKI-ROAs, or both.
The State of Routing Security in Ukraine and Russia
It is difficult to prepare for a future cyber attack when one is already underway. When an attack is in progress, it’s likely too late to initiate any major technology change. That’s why readiness and preparedness are so important. So how are the two countries doing on routing security?
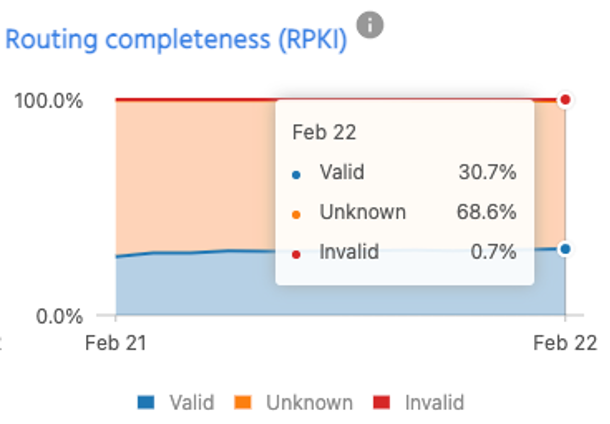
For Ukraine, looking at routing information for both IRR-route objects and RPKI-ROAs, the situation is not very good. Using data from ROAST and IHR, there is no major change in either route object or ROA creation even after multiple attacks in the country.
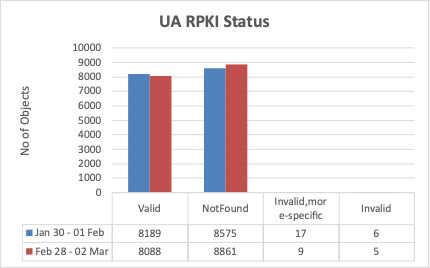
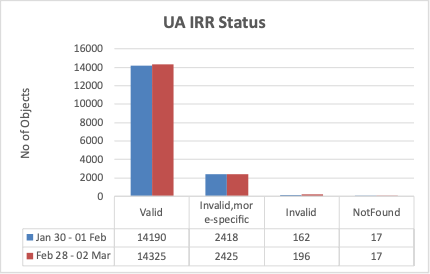
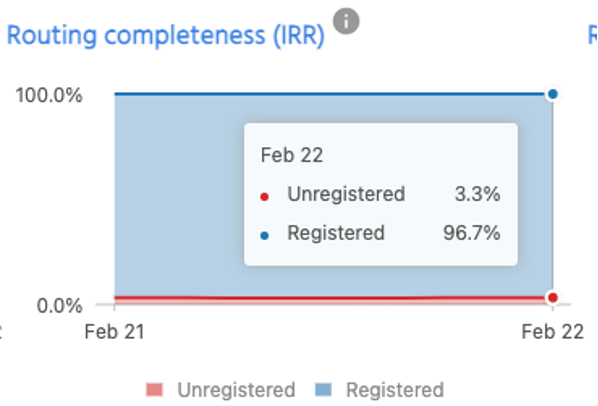
First, the good news: around 85% of route advertisements are covered via IRR-route object to avoid BGP hijacks. However, that leaves 15% not covered via IRR. The situation is much worse for RPKI-ROAs, as almost 52% of route advertisements are either completely not covered or incorrectly defined, which makes all these routes vulnerable to hijack.
Just like Ukraine, Russian networks are also not showing a great deal of success in terms of ROA adoption.
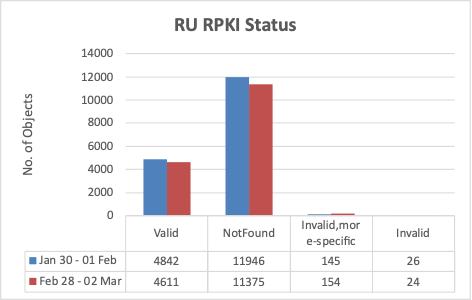
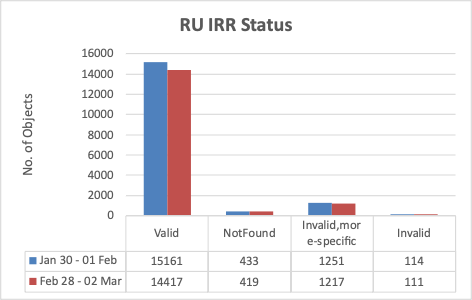
RPKI-ROA adoption in Russia is around 30%, though IRR-route object adoption is close to 96% which is very good.
Protecting Your Network
To protect against BGP hijacks, networks must create valid IRR-route objects and create valid RPKI-ROAs.
As mentioned earlier, there are many network operators that actively filter based on IRR-route objects, and some also filter on the RPKI to drop invalid ROAs. This is a good sign that when (not if) an incident occurs, the impact can be minimized because the networks in the middle take proper action to mitigate further damage.
While having IRR-route objects is good, it doesn’t guarantee protection from BGP hijacks or that if a hijack does happen it won’t propagate globally. Most route object-based filtering is done either at the time of connectivity or at some very high random intervals. On the other hand, RPKI-based route origin filtering is almost instant (the only delay is because of ROA propagation).
The key takeaway: it is important for networks in Ukraine and Russia –and everywhere else—to create both IRR-route objects and RPKI-ROAs for all the advertised routes of their network to guard against any BGP hijack attempt.
When the Internet goes down, ordinary citizens are the ones most impacted. As the Internet Society’s Andrew Sullivan notes in a recent blog post, the many people all over the world living under conflict should have access to the Internet. It is a tool to help them understand what is going on, and to communicate their struggle.
Now, more than ever, people in the two countries and beyond rely on a secure and resilient Internet. That is why MANRS is so important. Please join us.
Leave a Comment