The United States Government Can Take Lead in RPKI Deployment
Since 2019, the use of Resource Public Key Infrastructure (RPKI) has drastically increased across the global Internet. RPKI is a method of cryptographically assuring a network is authorized to originate routes to a specific set of network addresses.
We’ve seen large, yearly improvements in RPKI deployment, with the percentage of prefixes that can be RPKI validated jumping from 18.6% in December 2019 to 41.5% in December 2022 (Table 1). By the end of 2023, more than half of the Internet is expected to be RPKI-enabled.
As the proportion of routes with registered Route Origin Authorizations (ROAs) continues to grow, the effectiveness of techniques like Route Origin Validation (ROV) will continue to grow.
| Global Networks | of RPKI valid prefixes | of RPKI unknown prefixes | of RPKI invalid prefixes | % of RPKI valid prefixes |
|---|---|---|---|---|
| Dec 2019 | 167,489 | 725,905 | 6,463 | 18.613% |
| Dec 2020 | 270,594 | 706,056 | 3,553 | 27.606% |
| Dec 2021 | 372,259 | 697,573 | 4,883 | 34.638% |
| Dec 2022 | 472,027 | 660,010 | 5,133 | 41.509% |
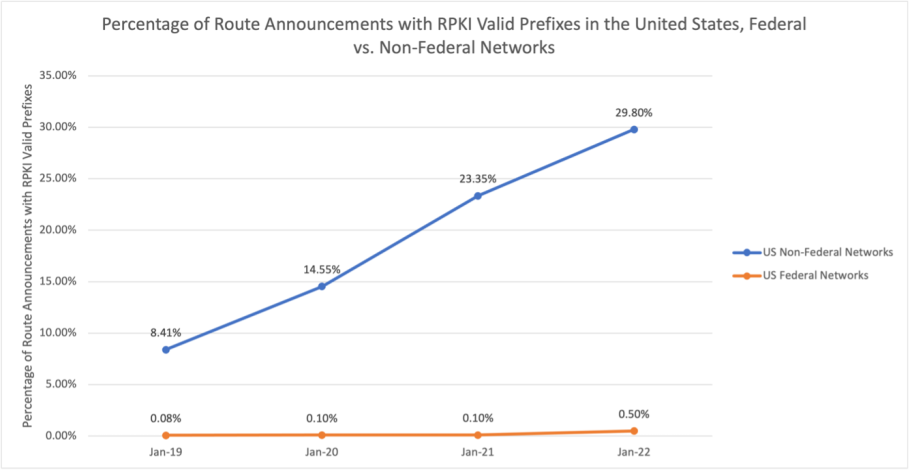
Even the United States, which has historically lagged far behind the global average on RPKI deployment, is beginning to catch up with the global average. In the last four years, RPKI adoption among United States networks has been growing at twice the speed of global networks. The percentage of prefixes that can be RPKI validated among US networks increased from 8.02% in December 2019 to 28.54% in December 2022. However, this growth isn’t consistent across all network types in the United States.
While RPKI deployment in the United States has quickly jumped from single digits to over a quarter of prefixes, one group of United States networks seems to be consistently lagging: networks run by the US Federal Government.
According to MANRS Observatory data, among networks run by the US Federal Government, only 0.5% of prefixes could be validated using RPKI in December 2022. Most prefixes from US Federal Government networks are unregistered using ROAs. Only 0.08% of prefixes announced from US Federal Government networks in December 2019 had corresponding ROAs registered and could have been RPKI validated. Despite some improvement between December 2019 – December 2022, the gap in RPKI implementation between US Federal Networks and US non-governmental networks increased significantly (Figure 1).
On 3 March, the Internet Society included these findings as comments to the United States Federal Communications Commission’s notice of inquiry on “Secure Internet Routing”. We called on the US government to improve the routing security of its networks and to make a concerted effort to deploy RPKI.
Governments are crucial stakeholders and trendsetters in cybersecurity. Whether intentional or not, cybersecurity standards set for governments often become de-facto industry best practices, especially in the United States. While non-governmental networks in the United States have improved significantly in RPKI deployment over the last four years, they still are behind the global average. If the US government can improve the routing security of its own networks and add routing security best practices to its procurement requirements, it may help greatly improve RPKI implementation not just in the United States but globally.
The MANRS Observatory provides us with the data to show the extent of the problem. The MANRS actions and implementation guides show a path forward. It’s now up to the United States government to make it happen.
Leave a Comment