Improve Your Security Posture With MANRS
Next-generation firewalls, anti-virus and anti-malware software, Intrusion Detection and Preventions Systems (IDPS), and various policies such as zero trust are all common features of modern security plans to defend networks. Before implementing these features, security experts will often carry out threat modeling to identify and prioritize all possible threats to a network or system.
Some threats that are often overlooked in this process stem from having weak routing security policies and practices. In this post, I’ll discuss the impact of these threats and how MANRS can assist those in the information security community to mitigate the risks.
The Vulnerability in Routing
Routing relies on trust and all parties being honest about which networks they connect to. Malicious actors can exploit this inherent vulnerability by configuring a router to declare or announce incorrect routing information that is appended in the global routing table — a database containing instructions of how to reach all visible networks on the Internet.
Using the example below (Figure 1), Network B could maliciously or erroneously declare itself as the final destination for Network D’s data. Instead of data destined for Network D flowing through Network B and then onto Network C and Network D, the data destined for Network D would terminate at Network B and be subjected to alteration, observation, or collection of user data without the appropriate knowledge or consent of its users. In routing, this type of incident is called a hijack where a network redirects another network’s traffic via incorrect routing announcements.
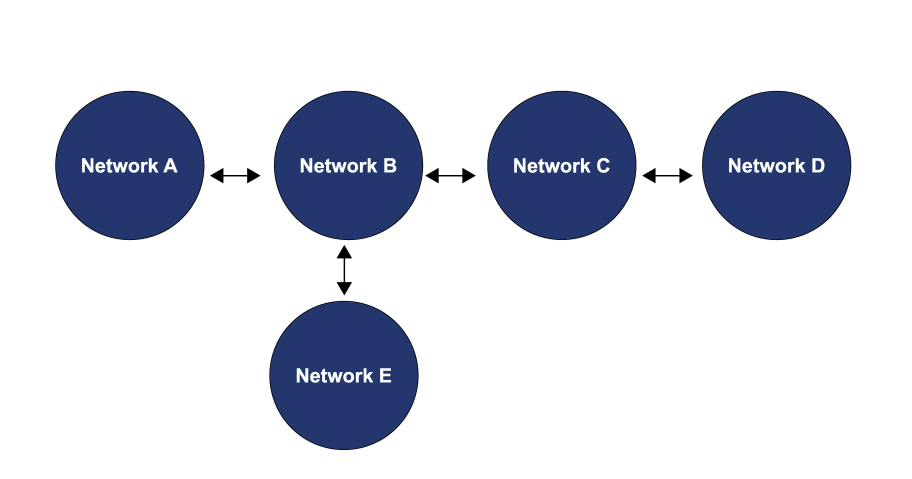
In the real world, the networks in the above example may be hosting e-government websites, university learning systems, enterprise networks, video streaming servers, hospital systems, banking systems, or social media websites. By using incorrect routing announcements, a malicious actor could:
- Take an entire network or country offline.
- Redirect unsuspecting users to malicious servers to collect data. In a recent incident, a network providing DNS services to its client was hijacked, and malicious DNS servers were served to clients. The malicious DNS servers then directed users to fake websites in control of the malicious actor.
- Initiate a Distributed Denial of Service (DDoS) attack by forging the source of network queries, resulting in thousands of responses being sent to a victim network which could be overwhelmed.
Unfortunately, routing incidents occur daily with varying levels of magnitude.
MANRS: Mitigating Routing Vulnerability Risks
Thankfully, there are current best practices defined by the Mutually Agreed Norms for Routing Security (MANRS) that mitigate the most common vulnerabilities attributed to routing security.
Network operators that adopt and conform to the MANRS actions help to improve their network’s security posture— the status of the various resources in place to protect a network and the data in it—by:
- Improving the accuracy of routing data — By filtering incoming and outgoing routing information, networks can help prevent incorrect routing information from being added to the global routing table.
- Reducing spoofing — Implementing anti-spoofing measures helps reduce falsifying network traffic by malicious actors.
- Maintaining current and accurate contact information – Globally accessible and up-to-date contact information facilitates quick reachability of the right people in the event a network has been compromised, has been hijacked, or is sending incorrect routing information.
- Adopting secure validation of routing information – There are facilities to help protect networks from falling victim to erroneous or malicious routing announcements on the Internet by cryptographically validating routing information. The Resource Public Key Infrastructure (RPKI) facilitates networks to use X.509 digital certificates to declare routing information about their network. Other networks on the Internet can then validate whether routing announcements received are valid. As more networks adopt these facilities, more accurate routing information is shared on the Internet, which subsequently reduces the chances of successful network hijacks. Read more about RPKI.
Does MANRS Work?
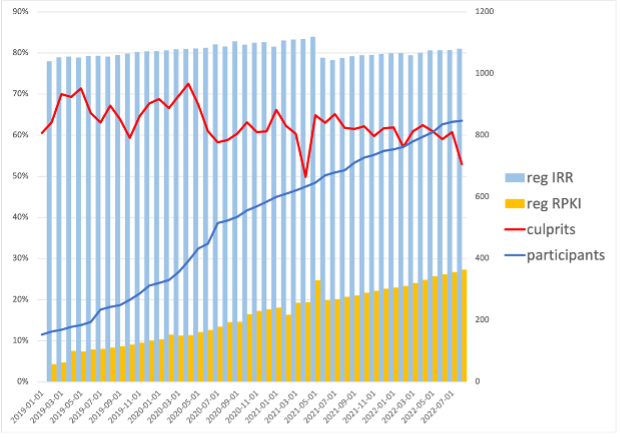
Data from the publicly available MANRS Observatory shows steady improvement in overall routing security among the nearly 1,000 MANRS participants (Figure 2). Adoption of secure validation of routing information (RPKI) increased to 77% and there was an overall decline in routing incidents.
The MANRS Observatory can be a valuable addition to current network security monitoring or Security Information and Event Management (SIEM) tools. The Observatory also has a publicly available API.
Read: There’s an API for that
Networks that sign up as MANRS participants receive monthly conformance reports related to their routing security status and elevated privileges on the MANRS Observatory. In addition, there are several training and mentorship opportunities available to further increase knowledge on routing security.
By being MANRS participants, networks can:
- Improve their security posture by reducing the number and impact of routing incidents.
- Improve their privacy posture by making it more difficult for their infrastructure to be hijacked or impersonated on the Internet.
- Join a community of security-minded operators working together to make the Internet better.
Learn how computer security incident response teams can improve global routing security.
Leave a Comment