Enterprises, Connectivity Providers, and Governments Must Work Together to Increase Routing Security
For most of us, the Internet works with a flick of a power switch and a click of a browser or app – we don’t really have to think about how it works or do much to make it work. This set-it-and-forget-it mentality filters down to the standards and protocols that make up the Internet, such as routing security. But we all have a responsibility to work together to prevent incidents like BGP hijacks, BGP leaks, and IP spoofing that wreak havoc on the Internet.
As Cloudflare’s Joe Abley described during last week’s Routing Security Summit,
“Routing security is not something you just turn on. It’s not a check box. It’s not just ‘deploy route origin validation’ or ‘publish ROAs,’ it’s a whole spectrum of activities.”
This need to take a holistic approach is practiced by 1000+ MANRS participants and is something that the program is trying to impart on enterprise networks and their connectivity providers who were the focus of the conversation during the session Routing Security as Supply Chain Security: Threats and Opportunities.
Below are some of the key points from the session, which you can watch a recording of below, including how:
- Enterprises need to take a more proactive approach to secure their whole supply chain from provider to data.
- Governments can both lead by example and encourage local networks to increase routing security.
- Connectivity and cloud providers can make it easier for their customers to implement best practices.
The Role of Enterprises
Enterprises – especially large ones – may be network operators themselves, and therefore have a responsibility to implement routing best practices. Smaller enterprises may not make many hands-on routing decisions, but they choose their connectivity providers through competitive bidding and procurement procedures where they can insert a demand for routing security.
“As an enterprise, you feel like you don’t have a lot of ability to influence [routing security decisions]. You’re not an ISP, you interact with only a relatively small number of ISPs … but I think the reality is that you do have an ability to drive that through your procurement process,” said Visa’s Matthew Davy.
Enterprises need the knowledge and tools to properly vet their connectivity providers, such as a set of standard questions and requirements to include in an RFP or procurement policy. “Financial services companies are trying to figure out how to enhance what they’re asking of their vendors, and if they can ask it in a very standardized way that becomes a whole lot easier than trying to go into detailed questions,” said FS-ISAC’s Linda Betz.
Large enterprises are more likely to have the depth and technical expertise to deal with these things in-house. As they solve these problems and share their knowledge, small and medium-sized enterprises can start to implement the same solutions.
The Role of Connectivity and Cloud Providers
When there are fewer network incidents causing outages, the network becomes more stable for the provider and its users. If we can reduce configuration mistakes and avoid accidental route leaks, providers can much more easily address the smaller number of malicious attacks.
Because of their extensive reach, CDNs have a responsibility to be extra stringent when they’re onboarding prefixes. The CDN’s job is to figure out how to onboard prefixes safely and securely at scale, and how to collapse the increasingly complicated supply chain to provide a key service to their customers.
“We have extremely detailed tutorials on how to enable IP space on AWS, but still we see a lot of errors – not only because the enterprise might have a low level of knowledge, but also because it’s actually pretty hard sometimes. It’s hard to untangle 20-year-old legacy documentation, or to figure out what IP space they have, or who holds it, or who is the person responsible for publishing IRR routes or maintaining the ROAs,” said AWS’s Fredrik Korsbäck.
Provider panelists discussed the ways they’re working with customers to update route objects and ROAs and with peering partners on spoofed traffic. “We have a rule that when you want to announce prefixes from us, that your administration is correct and you have ROAs; for our transit providers, we say you need to have proper routing administration and otherwise we will probably block you in filters,” said Liberty Global’s Antoin Verschuren.
“If you find a cloud provider or a network provider that’s willing to advertise your prefixes without these barriers in place, be afraid, because this is a provider that’s probably going to struggle to maintain the level of availability that you need,” said Joe Abley.
The Role of Governments
The Netherlands has added RPKI to its ‘comply or explain’ list, which is the list of standards that are required during government procurement processes on any agreement over €50,000. Because the government is such a large player and RPKI is now required, vendors are essentially forced to enhance their routing security practices. “If it’s on the required list, it becomes a default thing to add. It’s really helpful to have it on the comply or explain list,” said Benjamin Broersma from the Bureau of the Netherlands Standardisation Forum. He added that it helps to have tools available to help potential vendors understand if they’re meeting the standards, like having a simple compliance check on internet.nl for RPKI.
While other governments are starting to pay more attention to routing security, the Dutch government is the first we know of to include RPKI in official government procurement processes. This is a great example of leading by example and having a real impact.
The Role of MANRS
MANRS is a community of over 1,000 security-minded organizations committed to making the global routing infrastructure more robust and secure. MANRS outlines simple, concrete actions organizations can take, tailored to their role on the Internet.
Part of MANRS’ future is our work toward MANRS+, which is exploring the idea of creating a second, elevated tier of MANRS participation for organizations that comply with more stringent requirements and auditing, and building a better business case for enterprises and other connectivity customers to be a driving force in demanding better routing security from their providers.
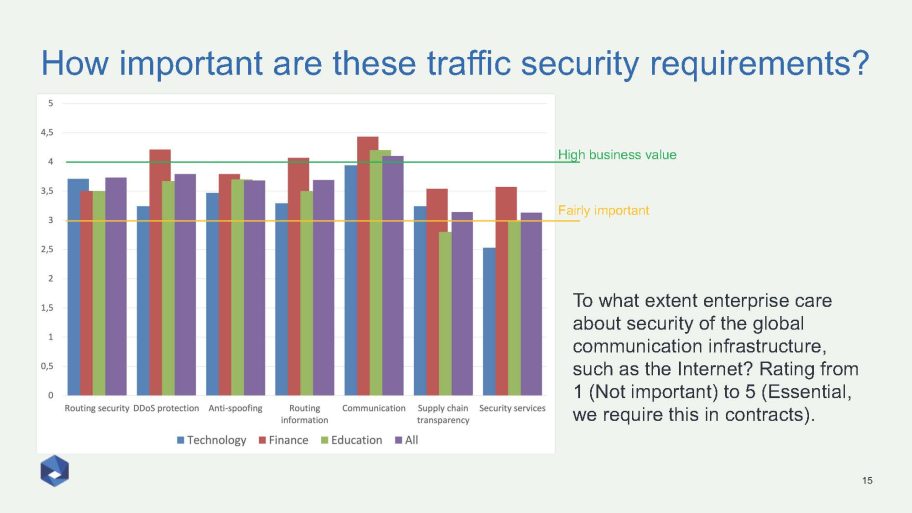
According to Andrei Robachevsky’s report on a recent survey to gauge interest in such a product, there is a high appreciation for the need to implement routing security best practices in the technology, finance, and education sectors (Figure 1). This feedback combined with ongoing Working Group discussions will shape the end product.
If you are interested in contributing your views and requirements, please join the MANRS+ Working Group.
Leave a Comment