Survey Shows Enterprises Value Routing Security, May Underestimate Their Ability to Influence Vendors
Enterprises increasingly rely on the Internet to store data and other digital assets, conduct operations, and serve customers. This significantly extends their security perimeter beyond physical boundaries and makes them vulnerable to infrastructure attacks, including routing security attacks.
Each year, thousands of incidents like route hijacks or route leaks lead to dropped, inspected, or diverted Internet traffic, or lead to DDoS attacks or strained infrastructure, all of which can cost a business time, money, and reputation.
After multiple incidents like the KlaySwap cryptocurrency theft, many enterprises understand the need to carefully vet their content delivery networks (CDNs) and cloud providers to ensure they secure traffic and safeguard customer data.
However, enterprises don’t always realize their Internet connectivity providers (or Internet Service Providers, ISPs) are the first line of defense to mitigate routing security threats. Recently a BGP leak at Angola Cables caused delayed or denied access to some sites and services for Australian users, with companies in affected data centers seriously impacted in their ability to do business.
There are often only a few providers between an organization and its assets or between an organization and its partners. If connectivity providers, CDNs, and cloud providers implement traffic security controls like those called for in MANRS, there’s a much higher chance of the data exchange happening securely and reliably.
Are Enterprises Aware of Routing Security as a Threat Vector?
The MANRS team recently surveyed a broad range of enterprises to better understand how organizations contracting Internet connectivity providers think about securing their traffic as it transits the Internet.
Specifically, we asked for feedback on what traffic security features they value from their connectivity provider. The following choices were provided:
- Routing Security. A connectivity provider maintains the capability to detect and mitigate the risk that a relying party’s traffic will be hijacked or detoured on networks they control as a result of a mistake or an attack. An example of such capability is filtering incorrect routing announcements or monitoring and mitigating routing incidents related to enterprise networks.
- DDoS attack prevention. A connectivity provider maintains detection and mitigating capabilities to reduce the risk of a volumetric DDoS attack. Examples are detection and blocking of attack traffic and coordination.
- Anti-spoofing protection. A connectivity provider prevents traffic from their direct customers or peers with spoofed source IP addresses.
- Maintaining routing information. A connectivity provider has accessible, complete, and up-to-date documentation of the intended routing announcements and other information on its routing policy that are essential for detecting and mitigating routing incidents on a global scale.
- Operational communication and coordination. A connectivity provider maintains a responsive NOC/helpdesk capable of coordinating and resolving traffic and routing security issues such as a large-scale DDoS attack.
- Supply chain transparency. A connectivity provider offers the feature “transparency of your communication supply chain” to its clients. This means that it provides its customers with additional information about itself and its upstream connectivity providers, such as administration settings (for example, legal ownership, third parties used, and applicable data laws) and security properties (for example, MANRS+ conformance).
- Security services. A connectivity provider offers security services helping the enterprise to maintain a strong security posture. Such services may include performing router security settings (for example, based on CIS benchmarks), routing incident monitoring, and reporting.
The rating scale ranged from “not important” and “nice to have” to having “high business value” and being “essential”. We asked respondents to evaluate it from the perspective of whether they were willing to pay a premium for these features.
Respondents Largely Aligned on the Importance of Routing Security Controls
The responses validate some assumptions we’ve made in the ongoing work for MANRS+, a second, elevated tier of MANRS participation for connectivity providers that comply with stringent traffic security and auditing requirements.
We received 88 responses from a broad range of industry sectors (Figure 1). Telecommunications, technology, finance, and education were most represented.
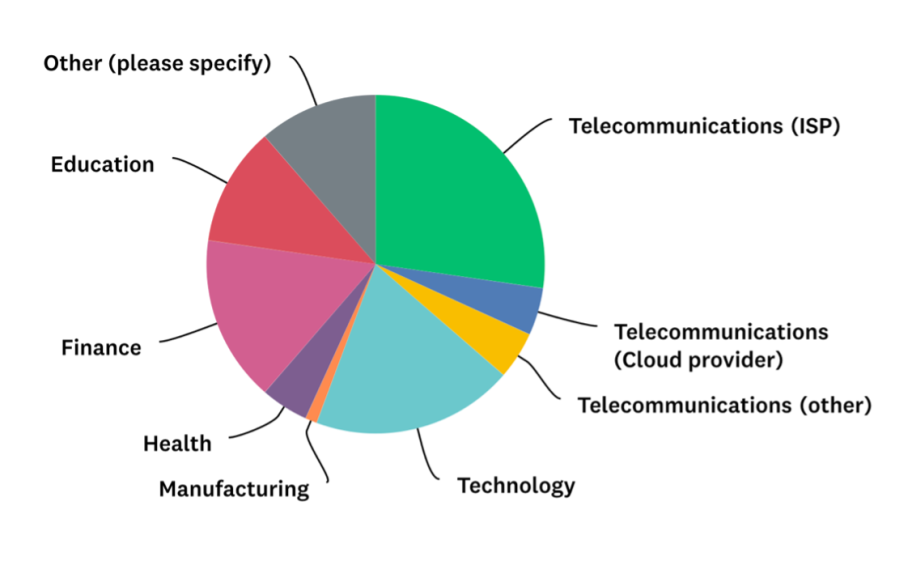
We zoomed in on specific industry sectors where we got many answers that could be considered statistically representative. Because the telecommunications industry was not the target, we concentrated on technology, finance, and education.
All the proposed security features got high ratings – on average above “fairly important.” “DDoS protection” and “Communication” scored the highest (Figure 2).
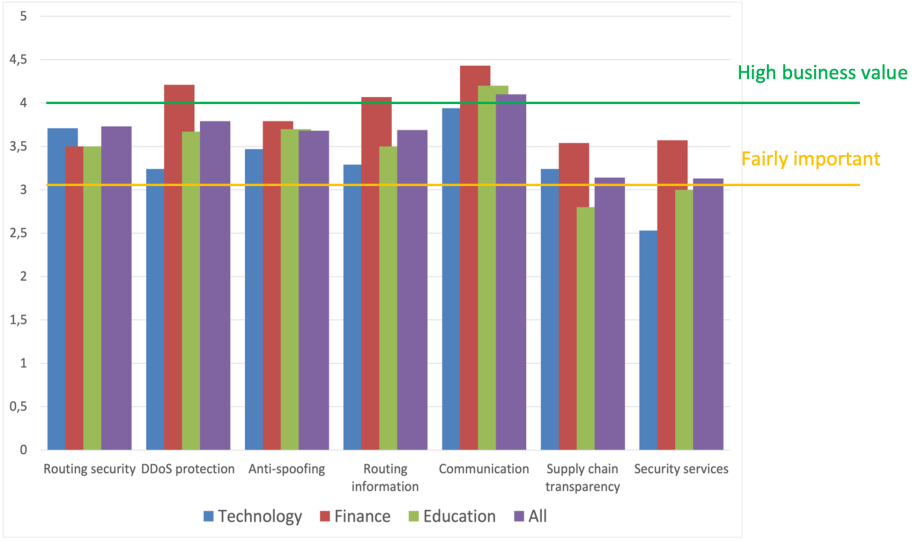
If we dig deeper into the results, we can see how different industries perceive such requirements.
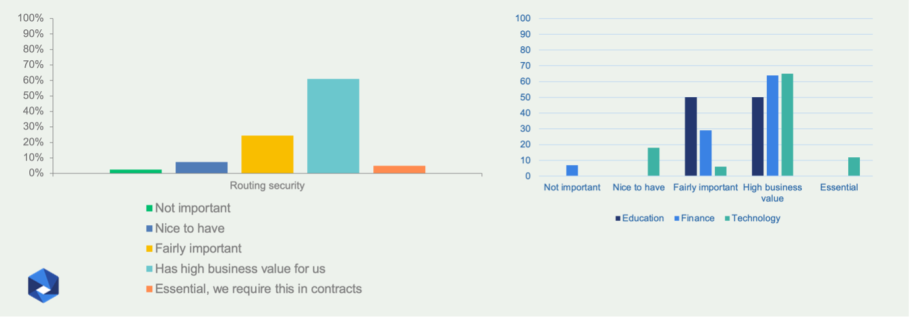
Respondents are largely aligned on the importance of routing security controls (Figure 3). For many, such requirements have high business value, although “fairly important” is also present. This may be because some respondents understand that a connectivity provider cannot guarantee routing security across the whole Internet. Another possibility is that routing insecurity is still not perceived as high risk.
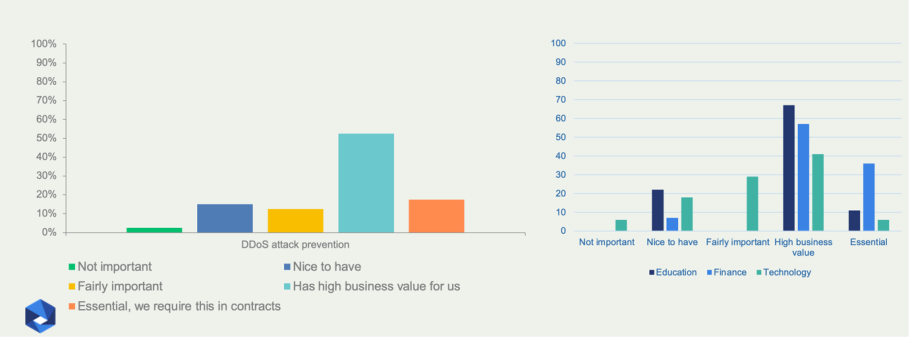
Most respondents rated the need for DDoS attack mitigation as having “high business value” (Figure 4), some deeming it “essential”, that is, a requirement in contracts (or making separate contractual arrangements for that service). It is of the highest value for educational institutions.
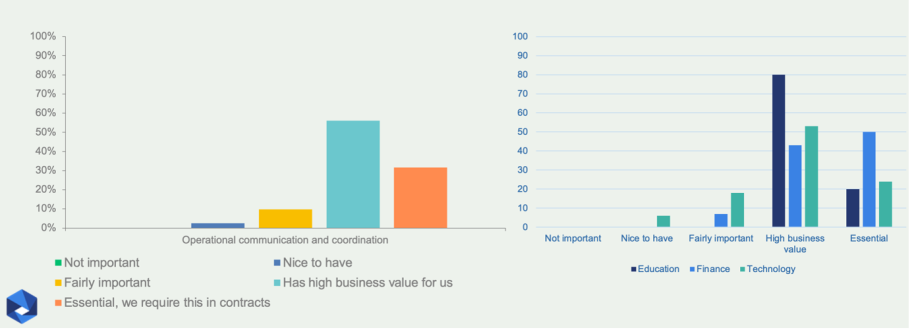
Respondents indicated the strongest support for operational communication and coordination (Figure 5). It is clearly a desired requirement by most and many require it in contracts, which is not surprising.
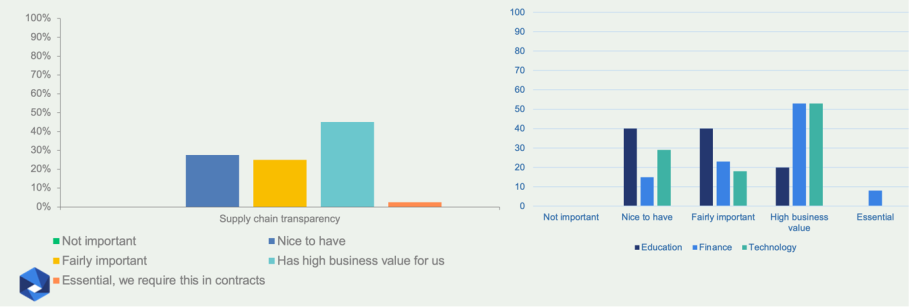
We observed a wide-rating spread for supply chain transparency (Figure 6). This may be partly because the requirement is less common and more complex to fully understand, especially if supply chain security is not really the focus of the infosec efforts of the organization.
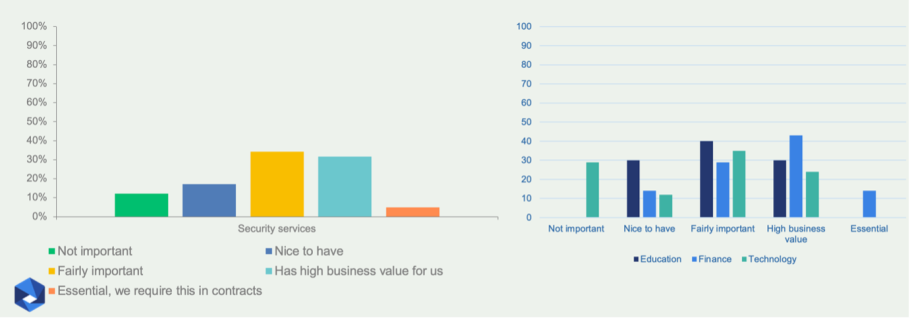
We see a similar pattern for security services (Figure 7). We envisaged that such services were most valuable for small companies that lack their own resources and expertise. However, the results show that mid-sized (100-1,000 employees) and even large (more than 1,000 employees) organizations value such services more than the small ones.
Enterprises Can and Should Drive Action
The survey shows a clear expectation and demand for a wide range of security requirements to achieve better routing security, and more generally traffic security, for enterprises. However, being at the edge of the routing system, enterprises often feel they can’t influence routing security decisions.
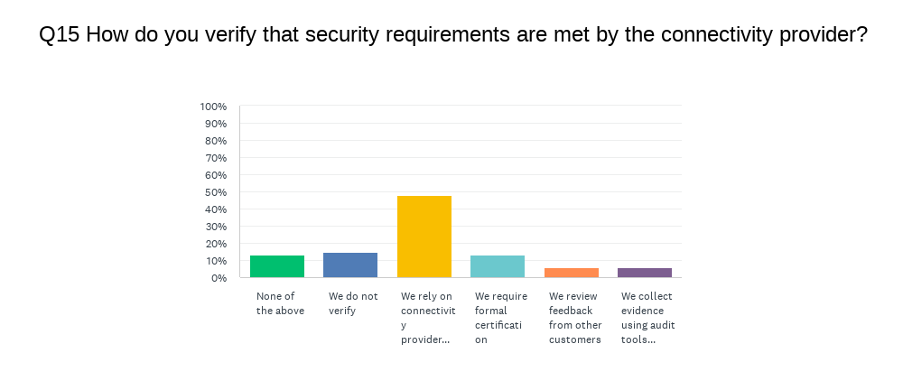
The reality is enterprises can drive action through their procurement processes. The problem is deciding what metrics to use when assessing a potential connectivity provider – how can you check that the security of their connectivity provider meets the requirements? As the survey showed, enterprises mostly rely on the explanations they receive from their connectivity provider, see Figure 8.
There are many security and certification frameworks that can inform you about the security posture of your providers, for example, ISO27K series, NIST-800, COBIT, and ITIL. However, they are extensive and supply chain security is defined in more general terms.
MANRS+ is an active Working Group within MANRS aimed at developing a security assurance framework that focuses on routing and traffic security specifically. Its main tenets are:
- Stronger and more detailed requirements in traffic security, mitigating a broader set of risks.
- Higher levels of auditing to ensure conformance.
- More focus on enterprise customer needs.
The idea is that by demanding compliance with MANRS+ from connectivity providers, organizations secure their own supply chain and stimulate improvements in the global Internet routing system, making the Internet more robust and secure.
Join the Working Group and MANRS.
Leave a Comment