Reflecting on “Routing security: fostering continuous improvement” at APRICOT2025
Routing security continues to be one of the most important areas in network operations. The industry is making steady progress in implementing routing security controls and, in particular, adopting technologies based on RPKI. However, challenges exist that slow adoption for both large and small network operators. Many of the challenges are related to network scale and topology, implementation costs, and supported features in network equipment. But others are related to the lack of customer awareness and demand concerted action to tackle the problem of routing security effectively.
Last week we organized a session on routing security at APRICOT where experts Anirban Datta (Earth Telecom), Mark Duffell (Telstra Limited), Muzamer Mohd Azalan (Telekom Malaysia), and Doug Madory (Kentik) shared their thoughts and experiences about major challenges to routing security and a potential road ahead. I had the honor to moderate this discussion and wanted to share some takeaways.
The Industry is Making Steady Progress
Routing security is improving overall due to the dedicated efforts of thousands of engineers at hundreds of companies. This progress is measured by the fact that half of BGP routes have Route Origin Authorizations (ROAs), and more than 2/3 of traffic (in bps) goes to destinations protected by ROAs. This is impressive progress given the fact that just two years ago only 1/3 of BGP announcements had corresponding ROAs and half of the traffic went to ROA-protected destinations, according to Madory.
Additionally, 83% of all Autonomous Systems (ASes) operating on the Internet have their intended routing announcements documented in the IRR system and about 40% have their ROAs in order.
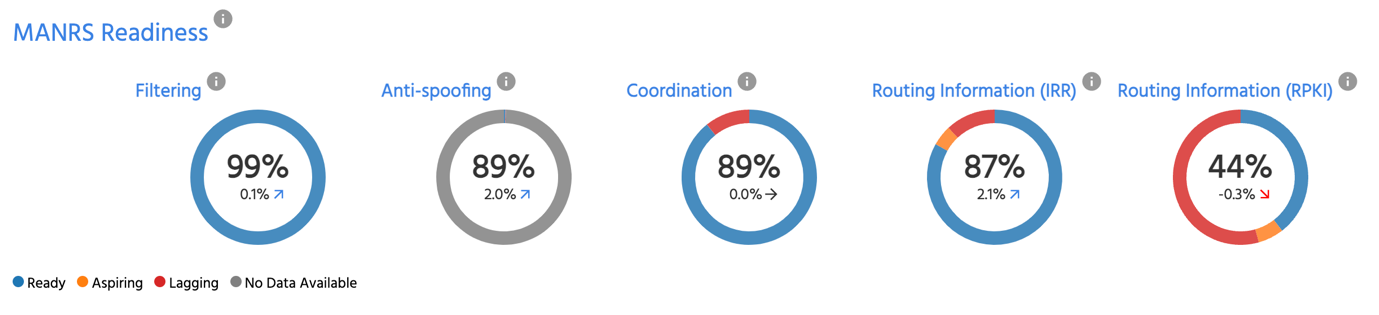
The impact, although challenging to measure directly, is visible: routing incidents caused by misconfigurations are continuously decreasing (see, for instance, a presentation from the Internet Intelligence Lab at Georgia Tech), and propagation of RPKI-invalid announcements is declining.
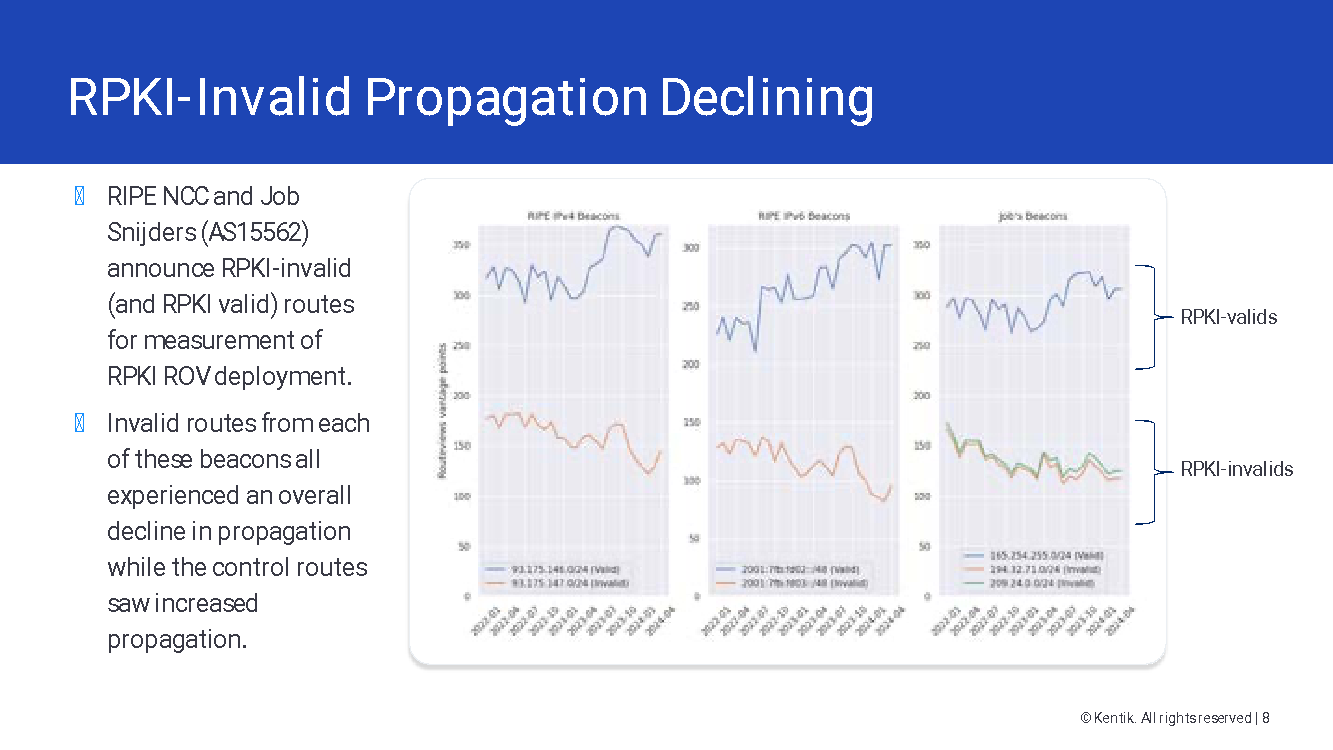
While this positive trend may create a perception that the problem is almost solved, there is much more to do. The global system is increasingly resilient, but mainly against misconfigurations. As Madory noted, a “determined adversary” can still exploit existing vulnerabilities as demonstrated by the recent attacks against cryptocurrency services.
We Need for More Customer Awareness, Education, and Demand
We kicked off the panel discussion by sharing the biggest challenges to improving routing security that network operators experience. One is bringing the customers along. Many customers lack awareness of routing security issues, and do not have the resources or expertise to implement effective routing controls. This is especially true in networks outside the telecommunication sector – small and medium enterprises, educational institutions, nonprofits, and local governments.
Things like prefix filters and anti-spoofing controls are most effective at the customer network level. For example, if the customer network does not ensure proper maintenance of its routing policy and intended announcements in the IRR and RPKI systems, it is much more difficult for the upstream provider to implement strong filters and almost impossible for networks farther away to prevent hijack attempts on these customer networks. But all too often, customers are slow to respond – or don’t respond at all – when reminded to register ROAs for its networks. Customers simply do not see network security beyond their own perimeter as their concern and responsibility.
The situation is aggravated by the fact that IPv4 space, because of scarcity, becomes more “mobile” – it is being leased and transferred, and networks announcing this space do not always have control over it from an RPKI perspective. For instance, the customer network may not have the ability to create or modify ROAs. Now, apart from the customer and its connectivity provider, a third party – a lessor – is sometimes required to take action to update a ROA or enable the user of the address space to make these changes.
Educating customers is therefore an important element of routing security. Because they may not be fully aware of these issues, customers often do not check the IPv4 lease contract for permissions and this then poses a barrier to the adoption of RPKI technologies.
Our key takeaway: Perhaps documenting a best current practice on IP address leasing, containing RPKI control as one of the items on the checklist next to common reputation checks, could help? Or a best practice in onboarding a customer? Perhaps this is something for the MANRS community to work on?
The ISP “Routing Security Toolbox”
With so much focus on RPKI in the operators’ community and in the media, it might look like this is the solution, a “silver bullet” to the challenges of routing security. All panelists agreed that turning on Route Origin Validation (ROV) doesn’t make their job done; it is one important validation step among other checks and controls that they must implement and maintain. Common practices, such as maxprefix limitations, protecting your BGP sessions with TCP-AO/MD5, General Purpose TTL Security Mechanism (GTSM), and ACLs must not be forgotten as they may become the weakest link in your network routing security.
Also, because RPKI adoption is not 100%, there needs to be a fallback to more traditional ways of performing validation, for instance by using the IRR system to build filters.
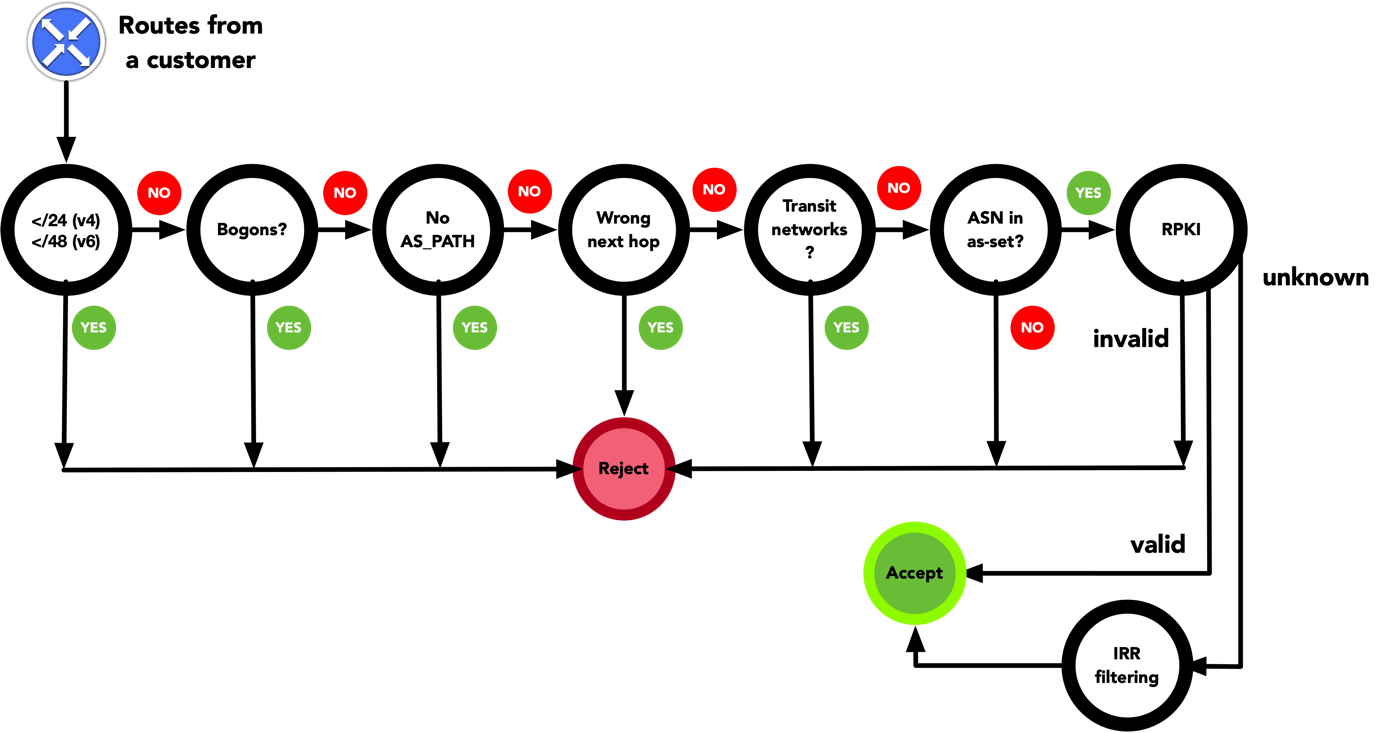
And finally, ROV is a first step in protection mechanisms based on RPKI. It doesn’t help to mitigate route leaks, which can be quite devastating. And it still allows impersonation by prepending a hijacked network to the path. AS path filters should be implemented, which will hopefully become easier with the adoption of ASPA.
The Way Forward
The panelists stressed that security is not a state, but a process. A continuous effort should be in place to ensure that routing security controls are optimally deployed and do not degrade but improve while following the changing threat landscape and advances in technology and practices. What mechanisms could be put in place to accomplish this?
One of the approaches that can help steer continuous improvement is embedding these controls and practices in the overall infosec framework of an organization. This could be especially relevant for customer networks and organizations outside the telecommunication sector. Routing security as a separate area is too little understood and does not usually show very high in an organizational security risk assessment. Routing security practices and controls have a much better chance of being implemented if they are part of a CISO checklist. One example of such an approach is an Internet Routing Security Profile based on the NIST Cybersecurity Framework originally developed by CableLabs and now being discussed in M3AAWG.
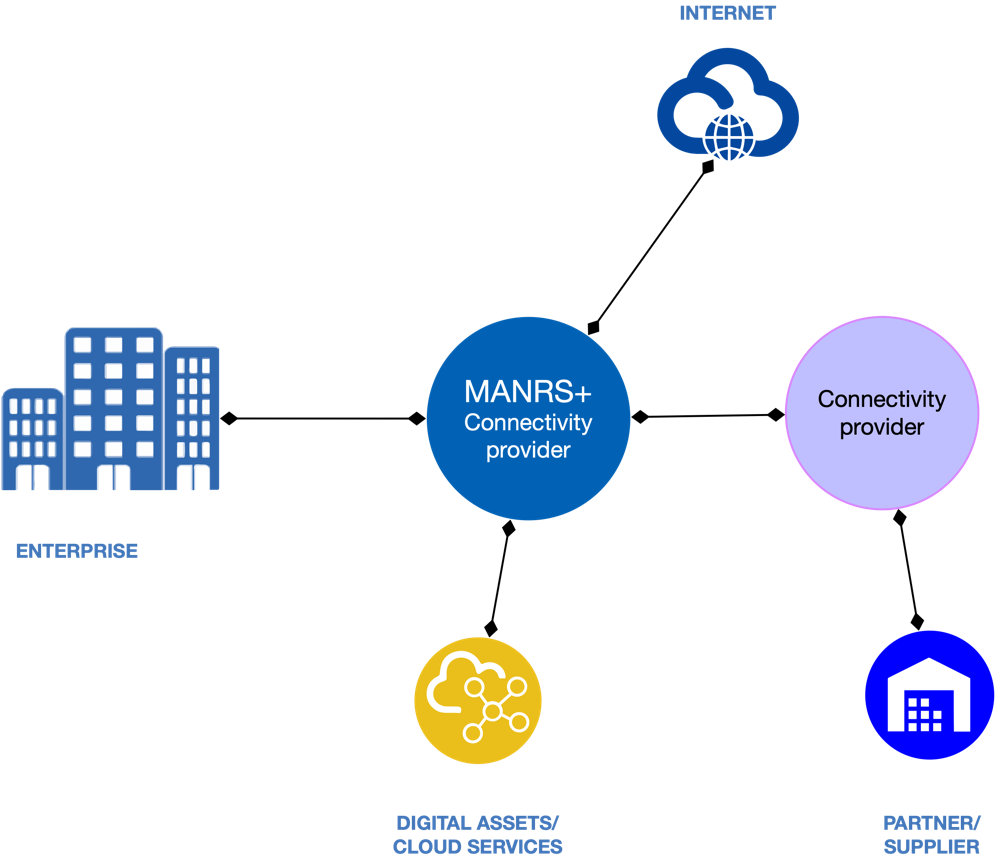
For edge networks, enterprises, and other organizations, whose digital assets are increasingly located outside the perimeter, having a secure connection to them and their business partners is a matter of supply chain security. And while the Internet is vast, there are typically only a few intermediaries in the enterprise’s distributed network. This means that by choosing their connectivity provider wisely, organizations can protect their supply chain.
To increase awareness and participation among enterprises, a second, elevated tier of MANRS participation is being developed by the community that requires connectivity providers to comply with more stringent provisions and auditing – MANRS+. It is a compact set of routing security controls and audit requirements that can be embedded in common infosec frameworks and referenced in procurement practices.
Following down this path may have an additional positive effect on routing security of the Internet as a whole by creating a stronger business case for routing security for providers while engaging their customers by raising awareness, generating demand, and providing necessary tools for security assurance.
I’d like to thank the panelists, again, for this excellent discussion at APRICOT 2025. It gives us much food for thought as we continue to work together to improve MANRS and the routing security landscape.
Leave a Comment