BGP Security in 2021
The Border Gateway Protocol (BGP) is central to how networks direct traffic across the Internet, and it provides the flexibility and scalability to accommodate Internet growth. However, like so many protocols, BGP was created before Internet security was a major focus and since there are no built-in security mechanisms in BGP, some issues do arise.
Occasionally, a network engineer may make a small mistake, or a bad actor intentionally redirects traffic. When BGP blindly accepts incorrect routing information and relays it across the Internet, bad things can happen and traffic can follow the wrong routes. These ‘routing incidents’ include route leaks, route hijacks, and IP address spoofing and each type of incident has the potential to slow Internet speeds, make parts of the Internet unreachable, or divert traffic through malicious networks for surveillance.
Every year, we investigate incidents that emphasize the vulnerability of the whole Internet routing ecosystem and how most of these incidents can be avoided by following the best practices called for in MANRS’ programs. Using data from Cisco’s BGPStream.com, which is one of the data sources of the MANRS Observatory and provides us information about suspicious routing events, in following sections we will examine some notable routing incidents in 2021.
BGP Hijacks
A BGP hijack, also known as a prefix hijack or a route hijack, happens when a network originates a prefix that belongs to another network without its permission, whether intentionally or mistakenly. These incidents are more frequent than it may first seem. In 2021, BGPStream collectors identified around 775 incidents marked as “Possible Hijacks.”
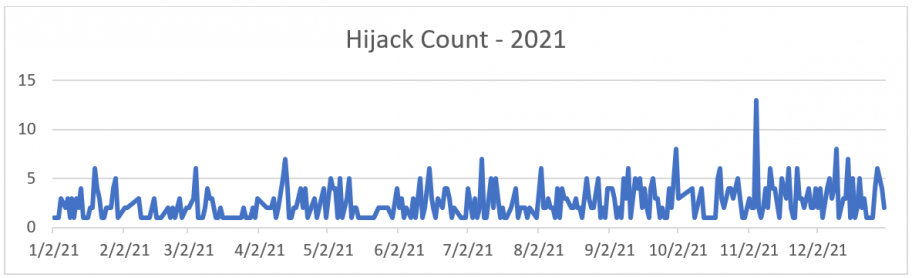
The good news is there were fewer incidents in 2021 than there were in 2020. But 775 is still far too high a number and there were handful of incidents that caused major disruptions globally. Here is a list of particularly major disruptions (selected on the basis of impact/number of prefixes) with a link to more information for each:
- October 25: AS212046 – MEZON – hijacked 3786 prefixes – Qrator Labs
- October 13: AS212046 – MEZON – hijacked 1029 prefixes – Qrator Labs
- September 21: AS62325 — HDHK – hijacked 89 prefixes – Qrator Labs
- May 18: AS48467 — PRANET – hijacked 454 prefixes – Qrator Labs
- April 16: AS55410 – Vodafone Idea Ltd – hijacked 30,000 prefixes – MANRS Blog
- February 5: AS136168 – Campana MYTHIC – hijacked Twitter prefixes – MANRS Blog
Qrator Labs is a strong MANRS partner that provides extensive commentary and factual details through their blog and Twitter feed; follow them on Twitter for up-to-date incident notifications.
BGP Leaks
A BGP leak, also known as a prefix leak or route leak, is another type of routing incident. Several types of BGP leaks are defined in RFC7908. As mentioned in the RFC, “the result of a route leak can be redirection of traffic through an unintended path that may enable eavesdropping or traffic analysis and may or may not result in an overload or black hole. Route leaks can be accidental or malicious but most often arise from accidental misconfigurations.”
While BGP leaks are often inadvertent router misconfigurations that are noticed and fixed quickly, they can be done intentionally to divert traffic through another network to scan it or perform man-in-the-middle attacks (where an attacker secretly relays and alters the communication path between a sender and receiver without changing the source or destination).
In 2021, BGPStream collectors identified around 830 incidents marked as “Possible Leaks.”
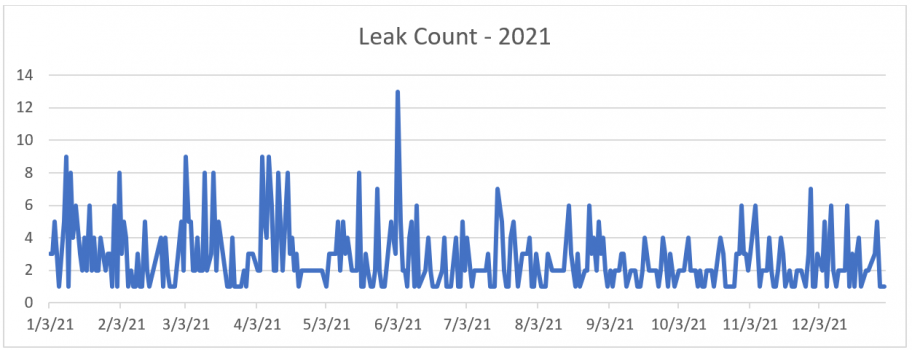
Just like BGP hijacks, there were some significant incidents that caused some disruptions (selected on the basis of impact/number of prefixes). Here are some of them:
December 24 – AS7633 – SOFTNET India – leaked 20,000 prefixes – Qrator Labs
December 24 – AS132215 – POWERGRID – leaked 112,000 prefixes – Qrator Labs
December 8 – AS10442 – VOZHD – leaked 32,000 prefixes – Qrator Labs
August 19 – AS265038 – JNET – leaked 11,000 prefixes – Qrator Labs
July 30 – AS137996 – WITGLOBALCOMMUNICATIONS – leaked 167,000 prefixes – Qrator Labs
June 3 – AS199599 – CIREX – leaked 26,000 prefixes – Qrator Labs
Limiting the Spread
The last quarter of 2021 was eventful for BGP hijacks and leaks, but interestingly BGPstream saw a decline in uptake of bogus routing information; that is, there was a decline in the number of network peers capturing errant routes from these incidents, essentially throttling their further propagation. To gauge how much the leak or hijack propagated over the Internet, we can analyze how many peers announced that bogus routing data to the BGPStream collector. The higher the peer count, the bigger the impact.
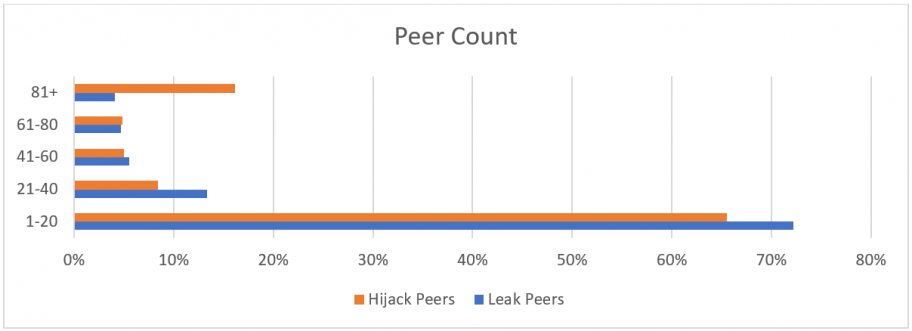
More than 70% of the total incidents were detected by fewer than 20 peers, meaning that most often bad routing data did not propagate far. It’s a good sign that when an incident occurred the impact was minimized because the networks in the middle took proper action to mitigate further damage.
Moving Forward
2021 was still marred by COVID-19, but many good changes happened from a routing security perspective. Many network operators took routing security seriously and started taking action to protect the global routing table. Specifically, a growing number of operators proactively put in place route filtering, created Route Origin Authorizations (ROAs), and started doing Route Origin Validation (ROV) — the latter two being essential pieces of the cryptographically protective Resource Public Key Infrastructure (RPKI) that can secure BGP announcements. The increase in MANRS participants in 2021 also clearly shows this shift in the community toward greater routing security.
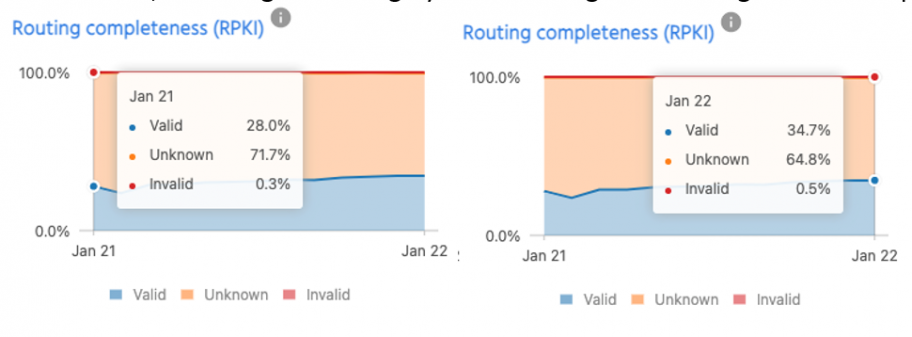
We still have a long way to go in deploying RPKI. With the global valid ROA count still hanging around 34%, it is not good enough yet to secure global routing with the help of RPKI. It will be a good sign once we reach 70% address space covered with ROA.
Convincing people to implement basic routing security measures is challenging. Often it is not technology that is the impediment, but more of a mental or psychological barrier to understanding why one would want to secure a network. It’s easy to assume if a network’s not broken that there is nothing to fix – but, in fact, routing still has major problems that aren’t always visible or predictable based on one network’s behavior, and it is every operator’s responsibility to contribute to the solution. Acting requires behavioral change, which comes from acknowledging the consequences of not putting in responsible routing security measures. (As you can see from the previous sections, some networks learn the hard way.)
The MANRS community is driving this behavioral change toward more secure routing. We now have more than 588 strong participants who believe in implementing basic routing security measures and are committed to convincing others to do the same. With the launch of MANRS Equipment Vendor program we have some of the top networking vendors who are supporting this initiative whole heartedly.
Leave a Comment